Red Hat Single Sign-on Integration with Ansible Tower
Red Hat Single Sign-on Integration with Ansible Tower
As you might know, Red Hat Ansible Tower supports SAML authentication (both N and Z) by default. This document will guide you through the steps for configuring both products to delegate the authentication to RHSSO/Keycloak (Red Hat Single Sign-On).
Requirements:
- A running RHSSO/Keycloak instance
- Ansible Tower
- Admin rights for both
- DNS resolution
Hands-On Lab
Unless you have your own certificate already, the first step will be to create one. To do so, execute the following command:
openssl req -new -x509 -days 365 -nodes -out saml.crt -keyout saml.key
Now we need to create the Ansible Tower Realm on the RHSSO platform. Go to the "Select Realm" drop-down and click on "Add new realm":
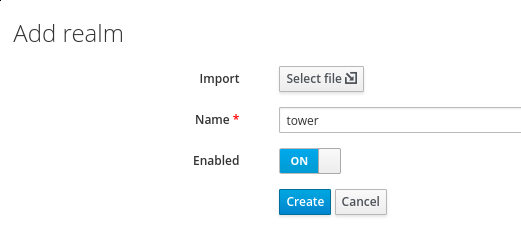
Once created, go to the "Keys" tab and delete all certificates, keys, etc. that were created by default.
Now that we have a clean realm, let's populate it with the appropriate information. Click on "Add Keystore" in the upper right corner and click on RSA:
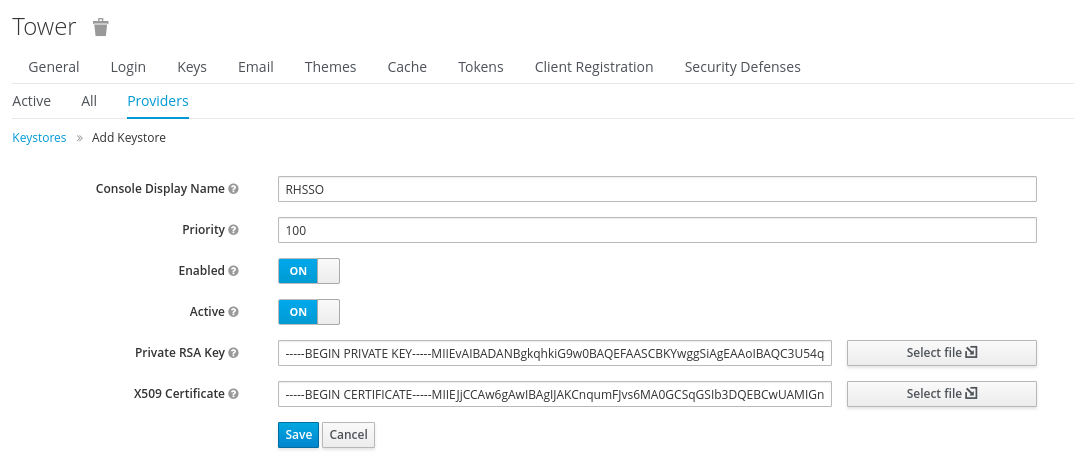
Click on Save and create your Ansible Tower client information. It is recommend to start with the Tower configuration so that you can inject the metadata file and customize a few of the fields.
Log in as the admin user on Ansible Tower and go to "Settings > Configure Tower > Authentication > SAML". Here you will find many fields (two of them read-only), that give us the information necessary to make this work:
- Assertion Consumer Service
- Metadata URL for the Service Provider (this will return the configuration for your IDP)
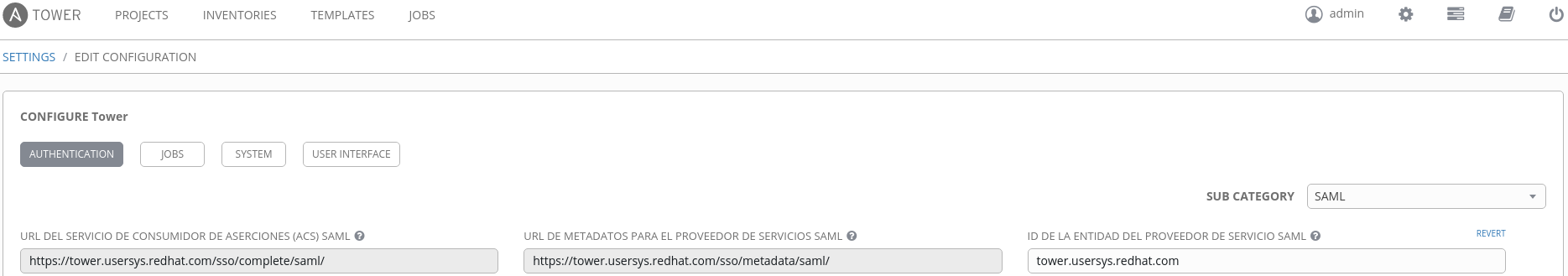
Now let's fill all the required fields:
- EntityID for SAML Service Provider:
tower.usersys.redhat.com(must be the same on RHSSO asclient_idname) - Pub Cert: use the saml.crt (
cat saml.crtand copy/paste) - Private Key: use the same.key (
cat saml.keyand copy/paste)
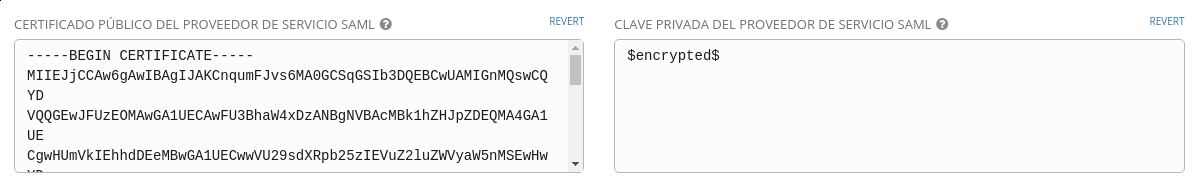
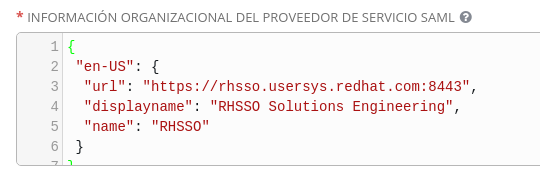
- Org info of Service Provider:
{
"en-US": {
"url": "https://rhsso.usersys.redhat.com:8443",
"displayname": "RHSSO Solutions Engineering",
"name": "RHSSO"
}
}
- Technical contact for SAML Service Provider:
{ "givenName": "Juan Manuel Parrilla", "emailAddress": "jparrill@redhat.com" }
- Support contact for SAML Service Provider:
{ "givenName": "Juan Manuel Parrilla", "emailAddress": "jparrill@redhat.com" }

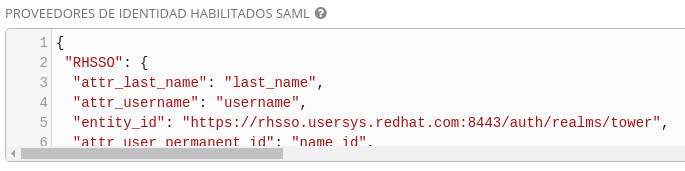
- Enabled SAML Identity Providers:
{
"RHSSO": {
"attr_last_name": "last_name",
"attr_username": "username",
"entity_id": "https://rhsso.usersys.redhat.com:8443/auth/realms/tower",
"attr_user_permanent_id": "name_id",
"url": "https://rhsso.usersys.redhat.com:8443/auth/realms/tower/protocol/saml",
"attr_email": "email",
"x509cert": "",
"attr_first_name": "first_name",
"attr_groups": "groups"
}
}
Note: To provide the x509cert field on the JSON, just execute this command and paste the result on the Ansible Tower interface:
sed ':a;N;$!ba;s/\n//g' saml.crt
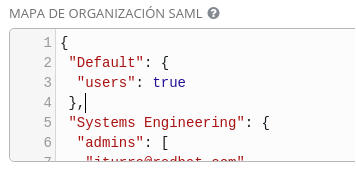
- Organization SAML Map:
{ "Default": { "users": true }, "Systems Engineering": { "admins": [ "acheron@redhat.com", "jparrill@redhat.com", "covenant@redhat.com", "olympia@redhat.com ], "remove_admins": false, "remove_users": false, "users": true } }
Recommended Steps and Things to Check
- RHSSO is the chosen name, which can be whatever you want and is not tied to DNS or server configurations. This is simply a visual marker.
- All the
attr_ fieldsare required to work and will be mappers on the client that we will create on the next step. -
Entity_idwill point to your realm. Go to your RHSSO realm through WebUI and in "General" you will see "OpenID Endpoint Configuration". Just click and catch the "issuer" field to fulfill theentity_id. - "For url" is a fixed field; put your
entity_idthere, followed by/protocol/saml. - If you generated your cert/key in RHSSO, you will have them in one
line. To convert to PEM format you can just wrap them in
"-----BEGIN CERTIFICATE-----" etc. and use
fold -w64to split the single line.
RHSSO Client Configuration
Now that you've configured SAML on Ansible Tower save the changes and start with the RHSSO Client configuration.
First, log in as the admin user on the RHSSO platform and go to the
"Tower" realm. From there, go to "Clients" and select "Create". Click
on "select file" to import the data that we already have on Ansible
Tower (to get the configuration execute this command from your laptop:
curl -L -k https://tower.usersys.redhat.com/sso/metadata/saml/).
Modify the Client ID by pointing it to tower.usersys.redhat.com, then
set the "Client Protocol" to SAML as displayed below:
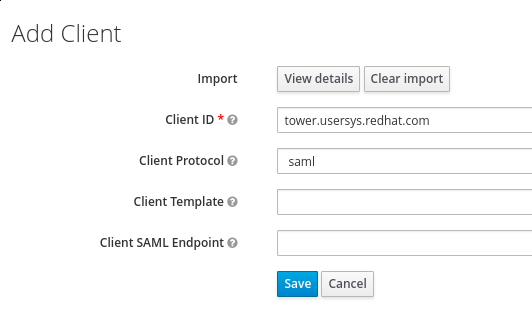
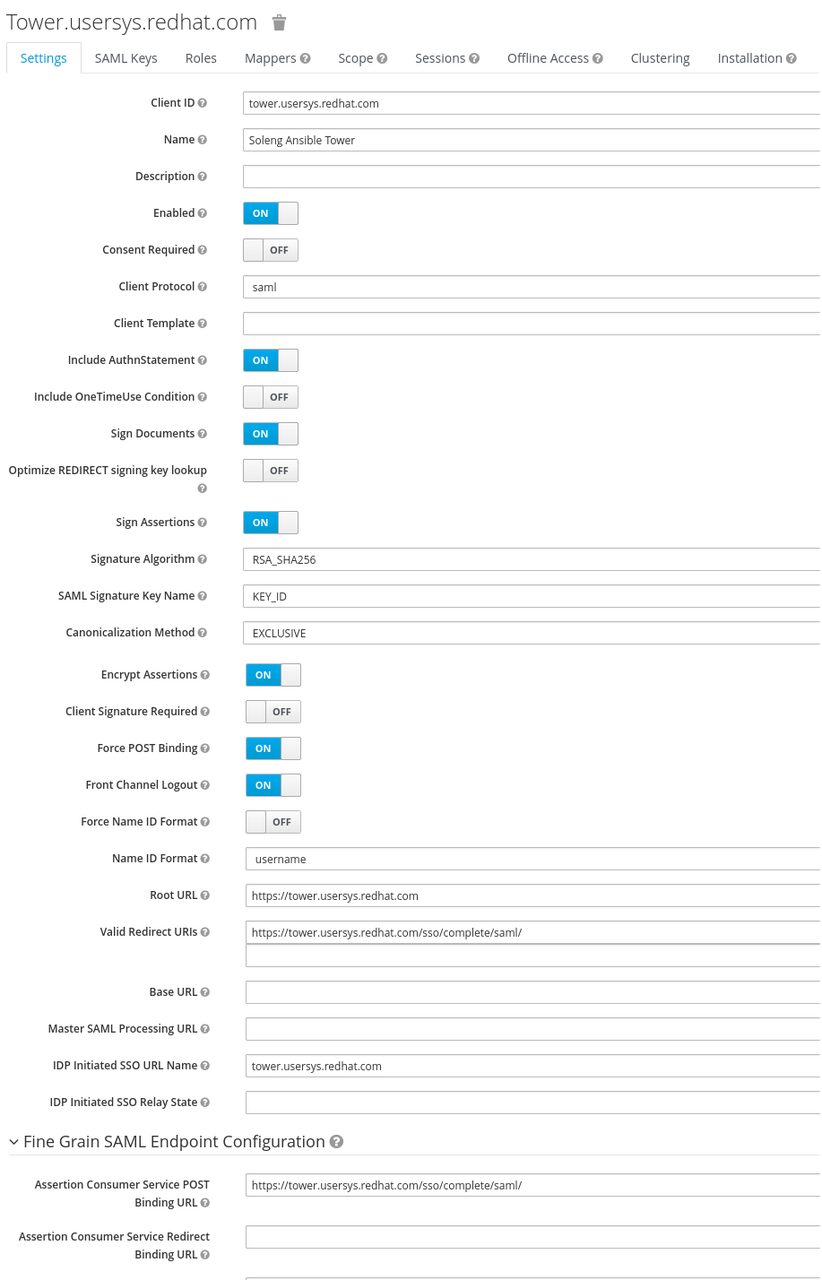
Next, fix the configuration to fit the following screenshot:
The last step to take is to create the mappers on Tower's RHSSO client. The purpose of this is to define the information that comes from your RHSSO, which will be mapped against Ansible Tower users.
To do this, we must go to Mappers tab:
Displayed below are the necessary mappers:
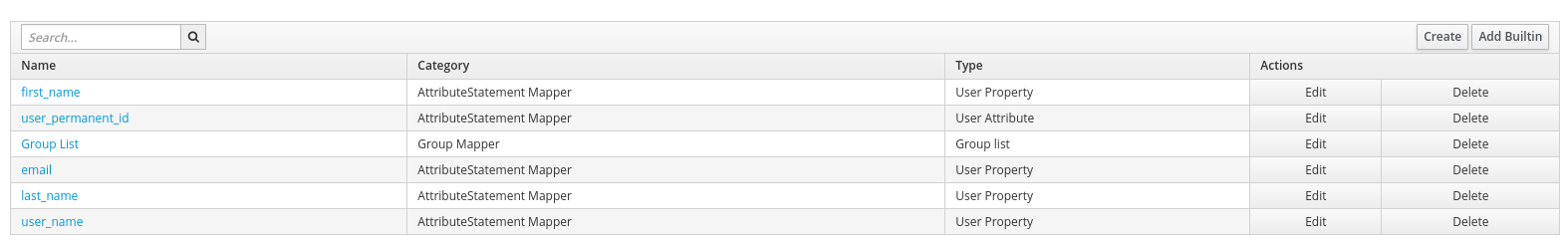
The following screenshot shows proper configuration of user name, last name, email, user ID, and first name:
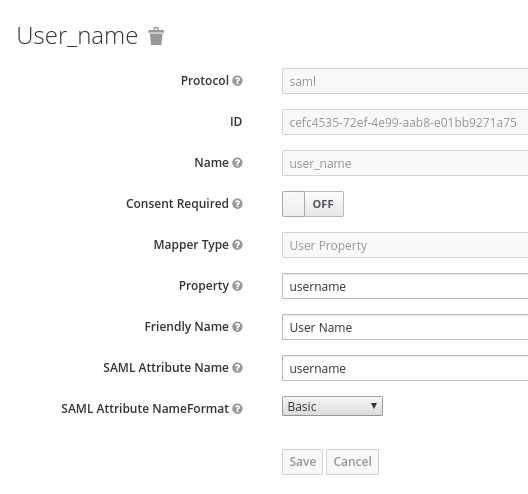
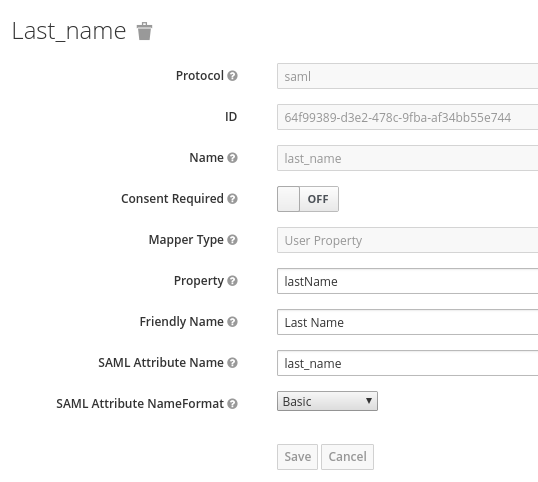
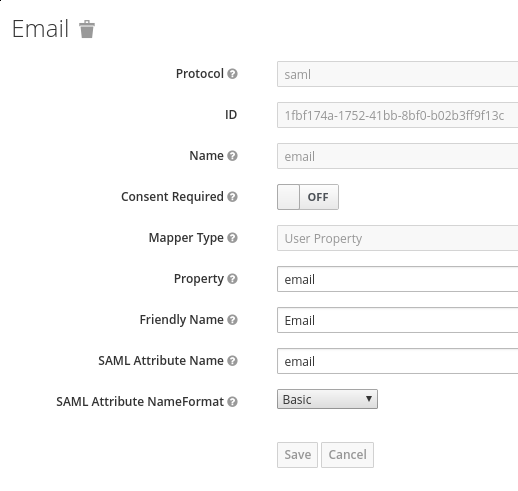
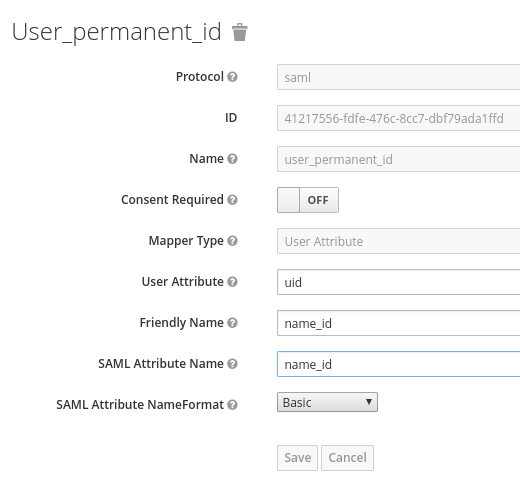
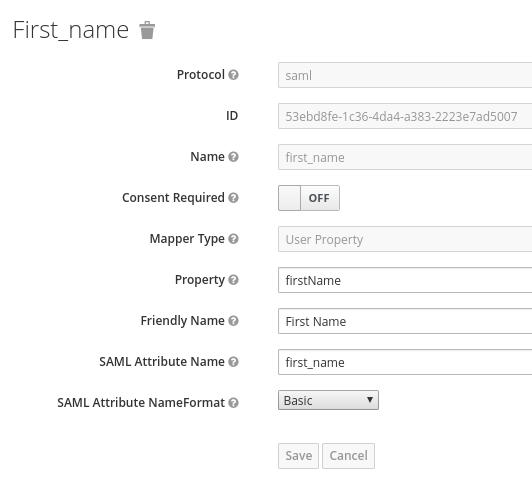
Note: "firstName" and "lastName" are case sensitive since they map the RHSSO user property.
Now you're all set!
Let's test with a user that we already have on our RHSSO (we have RHSSO
with a user federation against ldap.example.com). For testing
purposes, you can create a user on "Manage > Users" if you wish.
Now go to the Ansible Tower login page and you should see "Sign in With S":
Click on this "S" and you will be redirected to login on your RHSSO server:

And that's it!

Hope this was a helpful guide to Red Hat Single Sign-On integration with Ansible Tower!